GoalZero, part of NRG Energy, is a leading portable energy company which builds: PORTABLE POWER SOLUTIONS DESIGNED TO IMPROVE THE HUMAN EXPERIENCE GOAL ZERO ISN’T JUST A COMPANY, IT’S A BUSINESS CREATED BY PEOPLE WHO LIVE LIFE TO ITS FULLEST Here’s an example of a commerce experience where the focus on customer TRUST and environmental IMPACT drives the customer experience …
Building Augmented Reality (AR) Experiences for Retail and Mall Environments – Gamification
Here’s one the AR experience that I built while running product, customer success, data, and DevOps teams at Westfield/URW A good example of AR design and delivery around brand identity, engagement and gamification. Core idea: Use Brand identity as an anchor. The Westfield logo. I. Design your customer’s journey II. Provide unique center’s customization for marketing teams III. Registrations – …
Discussing Cryptocurrency Nano with a high school student.
Podcast: Play in new window | Download
Podcast: Play in new window | DownloadRecently, I had a quick call with a high school student who has become increasingly interested in blockchain technologies and cryptocurrency projects. He has expressed a lot of enthusiasm around Nano particularly its speed and limited transaction costs. https://nano.org/en/ This brief conversation was recorded for both including as podcast content but also utilizing the …
Building A Commerce Experience for An Outdoor Brand – Smith Optics
Smith Optics is a leading eyewear and cycling/motorsports brand focused on activities that protect but also enhance the experience of the activity. Here’s an example of a commerce experience where the focus on TRUST is central to the customer experience and brand proposition. Trust and Continuous (Agile Mindset) Impactful Experiences For Customers. Format: Bio Quick Wins Creation and Innovation Listen …
Feed The Machine Video using Offload Media From Delicious Brains
Are you staying hydrated? All media offloaded to Amazon S3 bucket. No image/video content stored within WordPress environment. Distributed content assets. Next test would be to use Contentful for Content API architecture. Headless CMS provides scalability and distributed content architecture for the many channels (FB, YouTube, Twitch), landing pages, and deployments of our content.
Zendesk – Today and Tomorrow
The customer support landscape today is evolving. What used to be a mostly phone, website, email, and a little chat, is evolving quickly. Zendesk has emerged as a critical player in the customer-centric support delivery model. Due to their user-friendly system, the dawn of their next customer platform is emerging through its new customer engagement platform strategy. Zendesk’s tomorrow is …
STILLNESS IS THE KEY – REVIEW- GOODREADS-EMBED
Here’s my first post to embed my GoodReads review. Stillness Is the Key by Ryan Holiday My rating: 4 of 5 stars Another great Ryan Holiday work where he continues to demonstrate his understanding of philosophical history. This work is probably his broadest approach to the idea of taking ownership of our minds. He references the Stotics, as he has …
The Power and Value of Team Services
What are team services? With Agile evolution, the notion of Squads, Guilds, and Tribes has sparked the development of operational models that support the cross-functional aspects of work today. Inside of enterprises, global technology teams are asked to significantly add efforts to innovate, grow and operate all consumer and customer touchpoints technologies in Web, Mobile, Retail, Franchising, Partner Commerce, Wholesale and ultimately …
2-Minute Warning Podcast: Episode 1 – Future of Frontend Engineering
Podcast: Play in new window | Download
Podcast: Play in new window | DownloadQuick huddle covering the future of frontend development. Performance Touchpoints and Frontend -Loading and Delivering. Data – Metrics. AI/Machine Learning. Augmented Reality – Conversational and Voice Interfaces. Personalization. React/Vue/WebAssemby/HTML code frameworks.
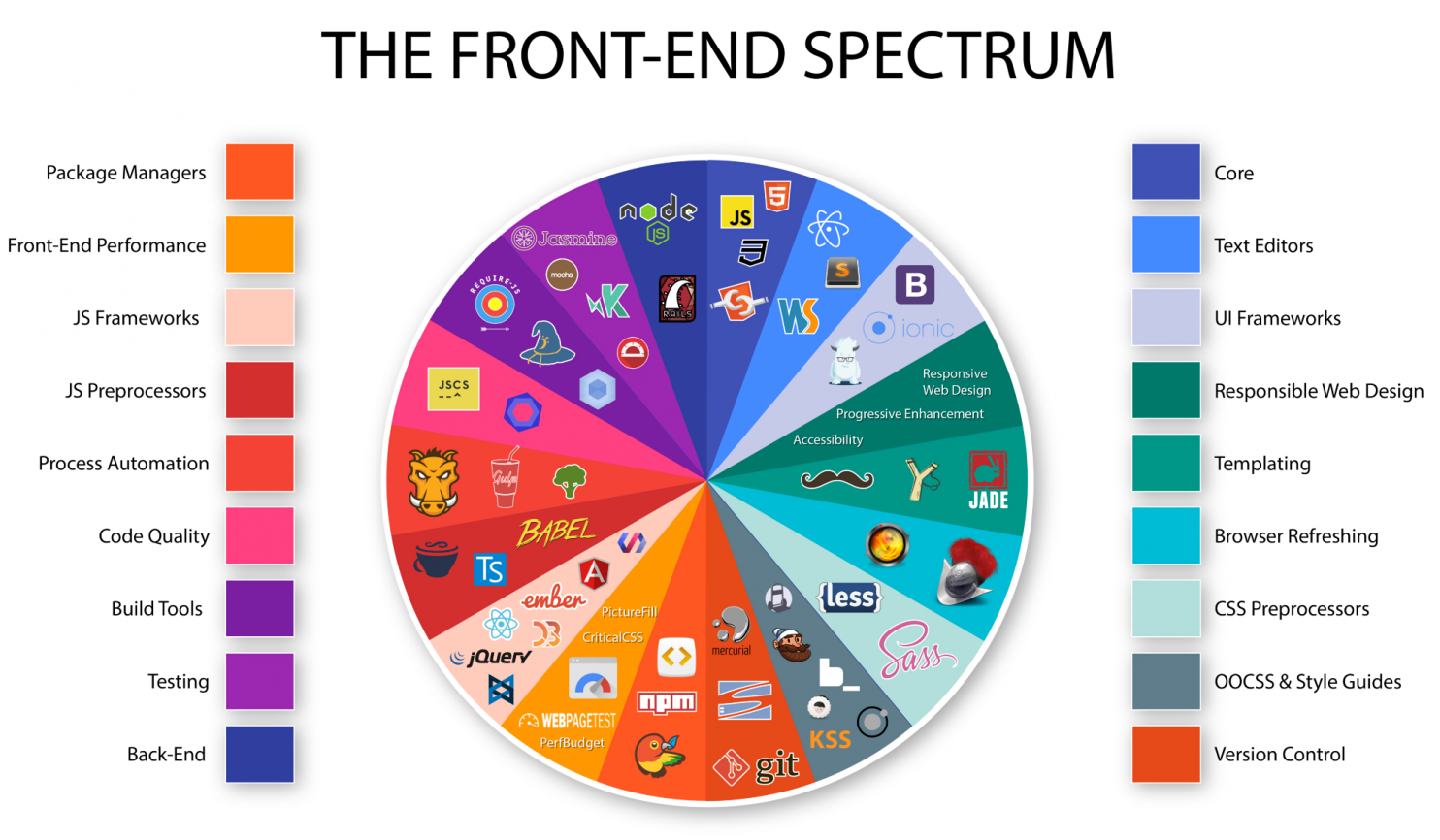
The Future Of Frontend Engineering
Let’s start with the basics. What’s Frontend engineering? Without the “In a galaxy far far away…” it started as HTML/XML to be interpreted by a browser. However, over time Brenden Eich (Now with Brave Software) developed Javascript and it has become an ingredient across the entire technology stack (i.e. Node.js). Hence the word “FullStack” was developed. A FullStack developer could …